Monitoring employee activity on macOS is hard. One of the most popular players in this space is Veriato with a close second of Ekran. Verioto is the owner of Cerebral and Vision, some of which was once known as SpectorSoft 360. There are several other on-premise and cloud hosted solutions out there, and most do not offer support for macOS Catalina. Fundamentally, Apple’s commitment to privacy and security is so strong on this level, that the market – at this time – has seemingly given up on offering capable solutions. That is not to disparage ActivTrak, it is a good product, but like all others it is limited on the macOS platform.
To use an employee monitoring solution, we have to deploy it first. While ActivTrak provides documentation on doing this with Addigy using the built in MDM, the documentation is deficient in key information that enables more flexible deployments. While we use Addigy MDM extensively, many of our sites use their own MDM solutions, including Meraki System Manager. Fortunately, the deployment is fairly simple, here is how it is done:
Information Collection
First, I collect the “BundleID“, “Team ID” and the privacy payload values for scthost.app and for scthostp which are hidden in /Library/PrivilegedHelperTools/. We contributed to the MacAdmins open-source community-maintained spreadsheet while posting this blog, and you can also find the information below.
TeamID:
sh-3.2# mdls -name kMDItemCFBundleIdentifier -r /Library/PrivilegedHelperTools/scthost.app com.bgrove.scthost
BundleID:
sh-3.2# codesign -dv –verbose=4 /Library/PrivilegedHelperTools/scthost.app
Executable=/Library/PrivilegedHelperTools/scthost.app/Contents/MacOS/scthost
Identifier=com.bgrove.scthost
Format=app bundle with Mach-O thin (x86_64)
CodeDirectory v=20500 size=133854 flags=0x10000(runtime) hashes=4174+5 location=embedded
VersionPlatform=1
VersionMin=658176
VersionSDK=658944
Hash type=sha256 size=32
CandidateCDHash sha1=648a30c3f4e9abbc4ba844aff5a1ad6508f560c7
CandidateCDHash sha256=3fbe683315ad586b13167378f7addd52c401df48
Hash choices=sha1,sha256
Page size=4096
CDHash=3fbe683315ad586b13167378f7addd52c401df48
Signature size=9032
Authority=Developer ID Application: Birch Grove Software, Inc. (B3MJ3FU6NZ)
Authority=Developer ID Certification Authority
Authority=Apple Root CA
Timestamp=Dec 22, 2019 at 11:54:11 PM
Info.plist entries=15
TeamIdentifier=B3MJ3FU6NZ
Runtime Version=10.14.0
Sealed Resources version=2 rules=13 files=18
Internal requirements count=1 size=180
Profile Payload:
sh-3.2# codesign -dr - /Library/PrivilegedHelperTools/scthostp Executable=/Library/PrivilegedHelperTools/scthostp designated => identifier scthostp and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = B3MJ3FU6NZ
The values you need are:
-
TeamID: “B3MJ3FU6NZ”
-
BundleID: “com.bgrove.scthost”
-
Designated: “identifier scthostp and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = B3MJ3FU6NZ”
Distribute Kernel Policy Extension Control…
Once I have values, I build and ship the Kernel Extension Policy Control and a Privacy Payload using my Mobile Device Management solution. Here is how that sets up:
| Parameter | Value |
|---|---|
| Profile Name | scthostp |
| KEXT Payload, TeamID | B3MJ3FU6NZ |
| KEXT Payload, BundleID | com.bgrove.scthost |
| Privacy Preferences Payload, Type | path |
| Privacy Preferences Payload, Path | /Library/PrivilegedHelperTools/scthostp |
| Privacy Preferences Payload, Code Requirement | identifier scthostp and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = B3MJ3FU6NZ |
| Privacy Preferences Payload, Accessibility | Allowed |
| Privacy Preferences Payload, System Policy All Files | Allowed |
| Privacy Preferences Payload, System Policy Sys Admin Files | Allowed |
Automate using your MDM Solution and then Addigy.
The rest is very simple:
-
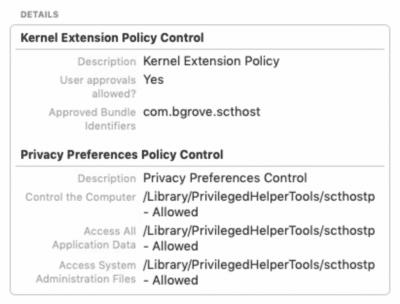
Push your MDM profile using your MDM system. Verify the payload arrives. You cannot install silently if this payload is not present. We recommend tagging machines and applying it only to the tag and expanding slowly. Profile should look like this on macOS:
-
Upload your PKG installer to Addigy’s Custom Software, create an install script via the automatic function.
-
Push the custom installer to desired machines.

